
The success of the digital transformation of organisations will require cybersecurity
Digital uses shape our way of producing, consuming and trading, as well as manipulating our uptake of knowledge before we make decisions. This digital intensification of both our personal and professional lives is being seen continuously in regard to the technology that is ever-present in our daily actions.
We take control of these tools, which were designed for intuitive use shaped by the careful observation of our behaviour.
Above all, such designers are looking to enhance the availability, reactivity and fluidity of the uses of digital information: ensuring that any technical limitations diminish, in favour of features which help and facilitate interactions between people, companies and public authorities.
This ever-increasing integration of technologies of information has been identified by the authorities of the European Union, as a priority, also to support growth, jobs and competitiveness at a global level.
They are seeking to ensure that this digital up-take is smooth and efficient within the 28 Member States.
This digitalisation certainly achieves value creation, but is also likely to find itself weakened by insufficient consideration of cybersecurity criteria.
This is crucially the case when equipment falls victim to hacking and when this is organised in succession in order to maximise the effect on production lines, financial exchanges or the activity of public services.
This digital exposure is all the more important in the industrial sector, which has in the past few years, been making up for lost time in terms of computerisation and is making use of more and more robots in its production lines.
According to the International Federation of Robotics (IFR), the sale of industrial robots will increase on average by 14% per annum in the years between 2019 and 2021. In the year 2018 alone, the industrial companies acquired some 421,000 new robots.
This represents an increase of 10% in comparison with 2017, which had already been a record year with its 30% increase against the year before.
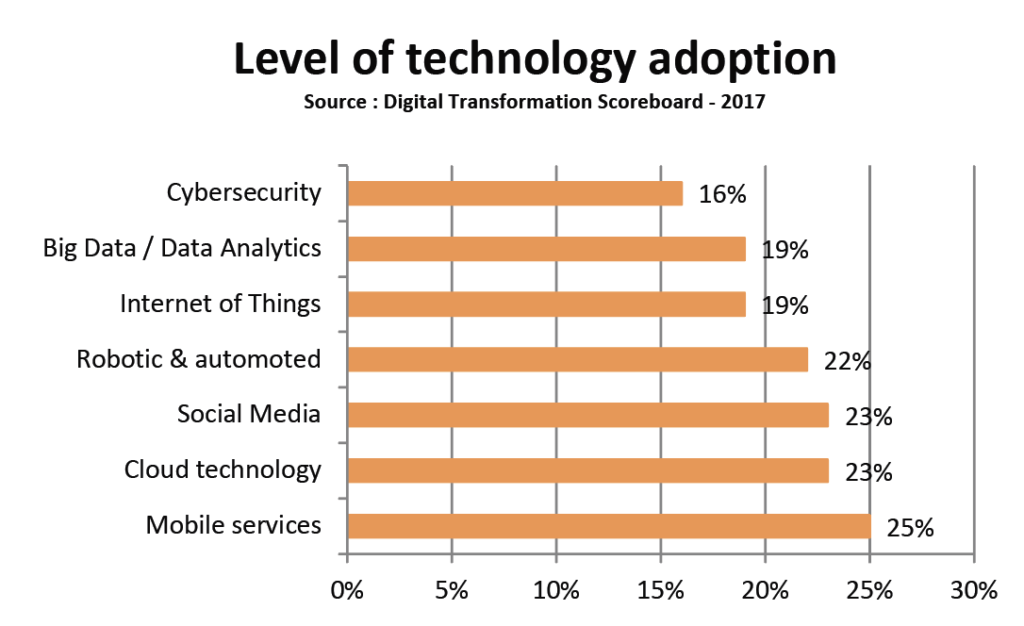
Security measures supporting digital transformation
A country like France has 137 robots for 10,000 employees; in South Korea, the figure is 710.
It is in this context that the Orange Cyberdefense experts have been active within companies since 2013, initially in major companies and increasingly in small and medium-sized enterprises, to support the security measures of the digital transformation of these organisations.
Relying on a considerable number of facts found during hundreds of audits carried out in the industrial sector by Orange Cyberdefense since 2013, we have established a ranking of identified weaknesses in terms of digital security.
Number one rank weakness identified would be taken up by the lack of detection capabilities. This prerequisite evidently limits the capacity to evaluate the very principle of possible security breaches of the company.
The lack of hardening of the information systems is the second point of weakness of industrial organisations which too often insist on using basic solutions without particular precautions, such as encryption, for example.
The same is true of the frequent use of Operating Systems, protocols and unsecured firmware. In any case, the management of human computer interaction control procedures leaves you wanting more.
For that reason, the continuous connection of the said Human-Computer Interaction (HCI) is generally the rule, without any real reflection in regard to the management of such practices.
This culture of sharing information is a decisive step towards greater security. In benefitting from the experiences of one’s peers, we are able to angle our strategic choices more effectively.
This assistance is very valuable in a context where pending decisions are made in a changing and often unstable environment.
This is the reason why Orange Cyberdefense prefers to take a partnership-based approach which gives its major customers the opportunity to exchange ideas peer-to-peer in order to share their expertise.
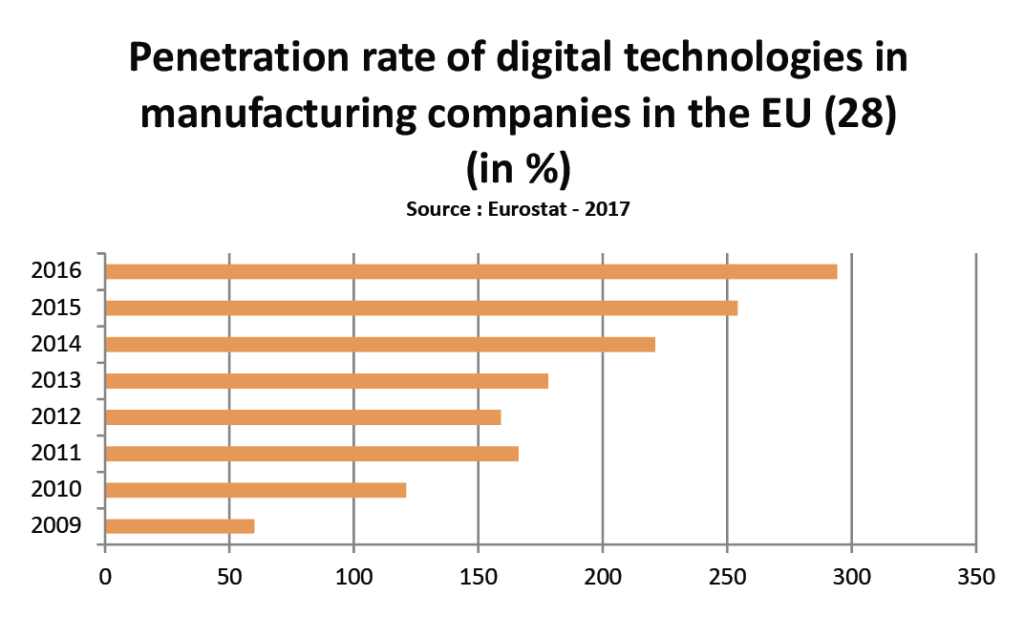
Integrating security measures as early in the process as possible
In order to support this unprecedented economic transformation, companies must be able to rely on advanced consulting and reviewing skills despite the diversity of technological delivery specific to each business sector.
It is also necessary to have a good command of the legal context in order to ensure the compliance of very demanding texts such as the EU General Data Protection Regulation (GDPR) or the Network & Information (NIS) Directive.
This makes it possible to advise on technical choices in the best possible way so that compliance process does not affect the competitiveness of companies.
It is also important to increase the overall awareness, competencies and security level across the European Union, reason why the Cybersecurity Act recently adopted at EU level is welcome.
In terms of cybersecurity management, one must be in the position of guaranteeing availability, integrity and interoperability of the data which is collected.
We ensure that we are present at each stage of the production cycle and exploitation cycle in order to verify in particular compliance with rules on data protection.
Monitoring for early detection of & response to attacks
Thanks to monitoring tools, notably nine Security Operations Centers (SOCs) which are spread across the world, we are able to ensure constant monitoring of companies’ computer equipment. Something to react as quickly as possible when unusual behaviour is detected: machine learning tools are fed continuously by the mass of technical information gathered on the infrastructure of companies.
This artificial intelligence assists analysts by developing response scenarios. Its algorithmic capacity ensures an exploitation of these billions of security events. This analysis is equally powered by all technical signals recorded on the telecom network of the group Orange. This presence on a global scale provides an unparalleled basis for observation among security service providers.
The sharing of information via the international alliance of Computer Emergency Response Team (CERTs), which Orange Cyberdefense is part of, usefully completes the decryption grid for malware in circulation. For this reason, the work of the epidemiology lab and of Signal Intelligence of Orange Cyberdefense adds a rare expertise in regards to the analysis of malicious software.
Like medical teams specialising in viruses, in the long-term they study these aggressive programmes in different technical environments.
This is done in order to understand their characteristics and the intentions of their developers: this empirical approach is useful in identifying attack strategies used by the hackers.
Their classification, informed by this analysis of the laboratory’s experts, reinforces their ability to anticipate digital aggressions.
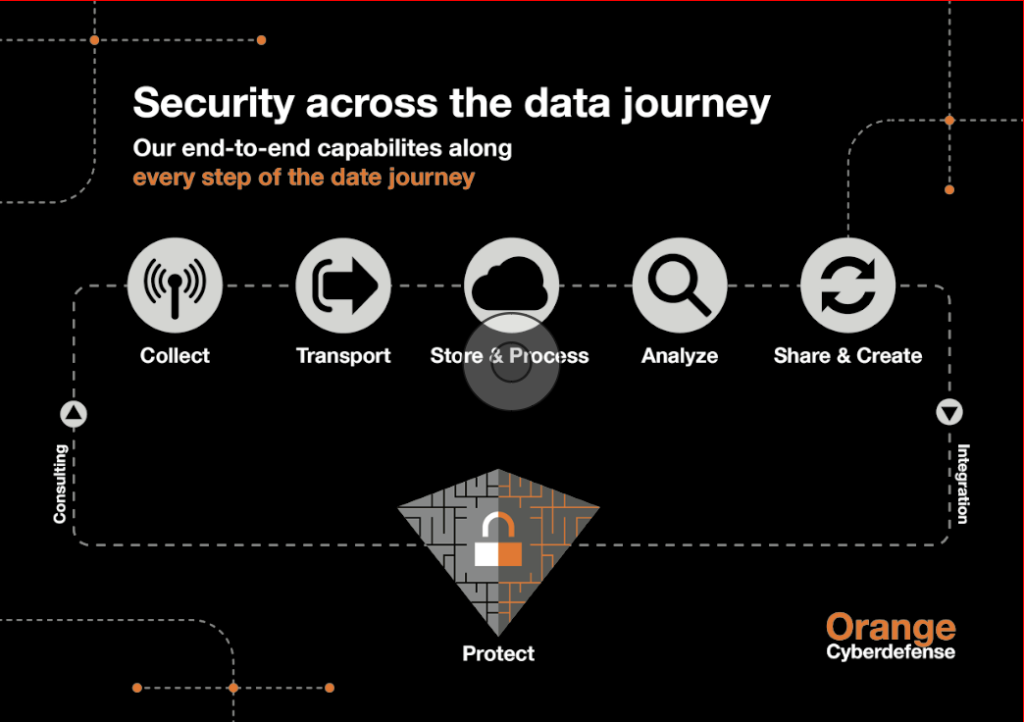
This expertise is gathered so as to act as early as possible before a cyber-attack begins or in order for measures to be taken early enough to limit its impact.
If the crisis couldn’t be prevented for technical reasons or because the company didn’t use sufficient protection devices, it is the responsibility of incident response specialists (CSIRT, Computer Security Incident Response Team) to be available to intervene as quickly as possible in the case of emergency regardless of the geographical location of the body in question.
This ability to mobilise experienced practitioners to intervene as quickly as possible and take appropriate action to protect the client’s interests, preserve evidence and promote a return to normality is a major differentiating factor in choosing one’s cybersecurity partner.
Orange Cyberdefense is particularly dedicated to ensuring this service, which supports decision-makers and companies at a time when cyber-attacks are at their most destabilising. Being the trusted partner in the service of protecting the essential data of companies is certainly part of Orange Cyberdefense’s missions.




